The JSOF research lab has discovered a series of zero-day vulnerabilities in a widely used low-level TCP/IP software library developed by Treck, Inc. The 19 vulnerabilities, given the name Ripple20, affect hundreds of millions of devices (or more) and include multiple remote code execution vulnerabilities. The risks inherent in this situation are high.
Ripple20 vulnerabilities are unique both in their widespread effect and impact due to supply chain effect, allowing attackers to bypass NAT and firewalls and take control of devices undetected, with no user interaction required.
Few risk examples including: data which could be stolen off of a printer, an infusion pump behavior changed, or industrial control devices could be made to malfunction. An attacker could hide malicious code within embedded devices for years. One of the vulnerabilities could enable entry from outside into the network boundaries; and this is only a small taste of the potential risks.
List of confirmed vendors till now including Aruba Networks, Caterpillar, Cisco, HP, HPE, Intel, Schneider Electric/ABC, Xeroex & others.
Vendors response
TREK announced providing patches for each issue that was reported by security research group, JSOF as mentioned in TREK website: https://treck.com/vulnerability-response-information/
Schneider electric announced that the company has not yet had the opportunity to completely validate all the specific research. However, having been aware of the vulnerabilities reported in the Treck TCP/IP stack & they have expedited a remediation for the vulnerabilities affecting the Network Management Card. https://download.schneider-electric.com/files?p_enDocType=Technical+leaflet&p_File_Name=SEVD-2020-174-01_APC_by_Schneider_Electric_Network_Management_Card_Security_Notification.pdf&p_Doc_Ref=SEVD-2020-174-01
Caterpillar announced working with the DHS and Treck to identify the impact. https://www.cat.com/en_US/support/technology/connected-solutions-principles/security/caterpillar-cybersecurity-advisory.html
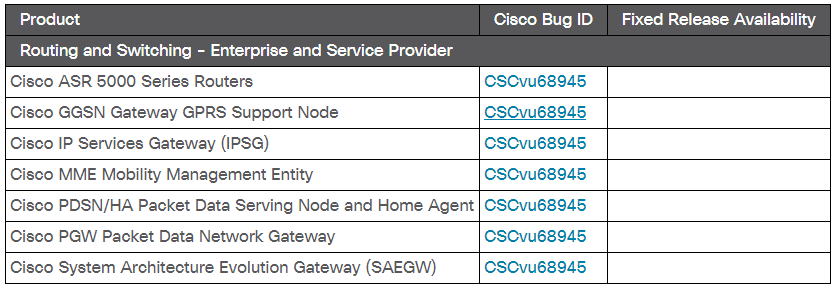
Cisco annoounced that exploitation of these vulnerabilities could result in remote code execution, denial of service (DoS), or information disclosure, depending on the specific vulnerability, also list of affected equipment have been listed as per below: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-treck-ip-stack-JyBQ5GyC